- Published on
How to use OAuth Proxy to protect your website
- Authors

- Name
- Sunway
- @sunwayz365
Abstract
You can use OAuth Proxy to protect your website if you do not want anyone to access your website in a public network like tekton-dashboard / admin-dashboard ... etc.
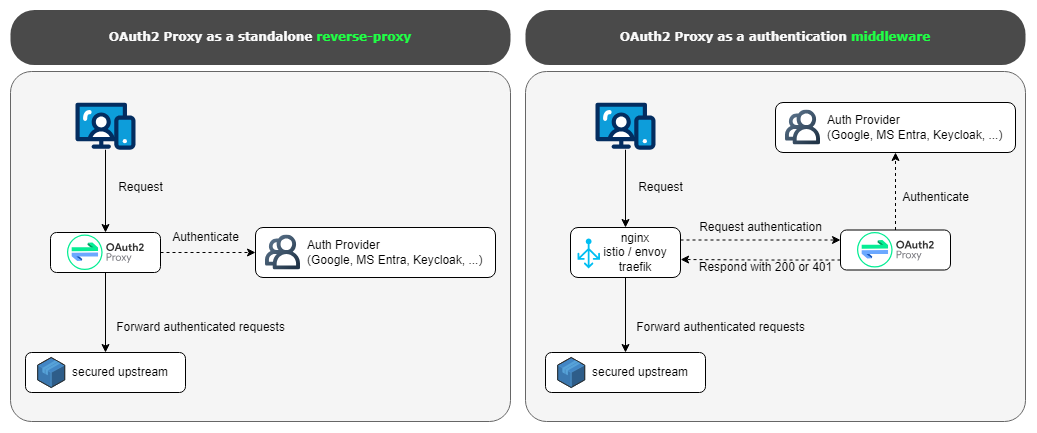
How it works
1: It can work as a reverse proxy 2: It can work as a middleware with Kubernetes Ingress/Gateway
Demo
This is a demo to show you how to use OAuth Proxy as a reverse proxy to protect your website in kubernetes environment with github provider.
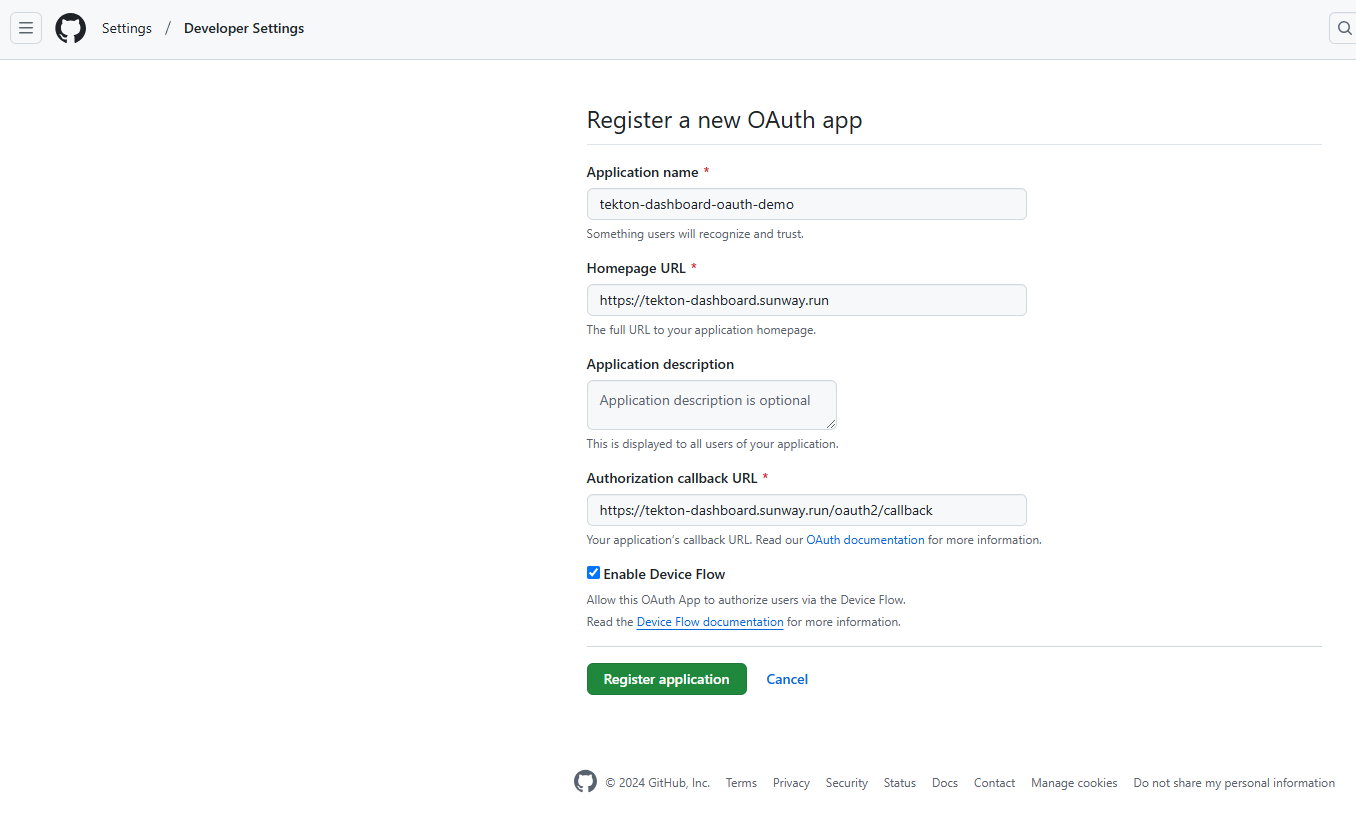
1 Create Oauth Apps
Settings -> Developer settings -> OAuth Apps -> New OAuth App
- Homepage URL:
https://tekton-dashboard.sunway.run - Authorization callback URL:
https://tekton-dashboard.sunway.run/oauth2/callback
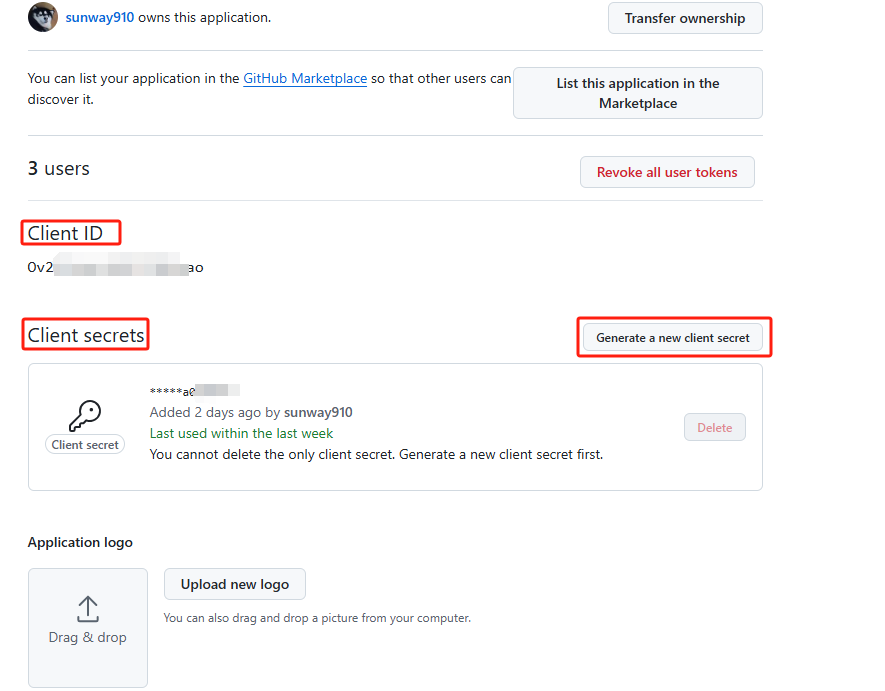
Enter Oauth App and click Generate a new client secret
2 Apply Kubernetes Manifests
- provider:
github, refer to https://oauth2-proxy.github.io/oauth2-proxy/configuration/providers/github - upstream:
http://<Tekton Dashboard Service Name in Kubernetes>:9097 - redirect-url:
https://<Your_Tekton_Dashboard_Url>/oauth2/callbacksuch ashttps://tekton-dashboard.sunway.run/oauth2/callback - cookie-secret: generate by
python -c 'import os,base64; print(base64.urlsafe_b64encode(os.urandom(32)).decode())' - email-domain:
*allows any email domain to login - github-org:
My_Github_Org_Name, please askgithub-org admin userto grant yourOauth Appsto read your org membership when you first login withhttp error code 5xx - github-team:
My_Github_Org_Name/Team_Name - ... etc.
Please check your ingress type
apiVersion: apps/v1
kind: Deployment
metadata:
name: tekton-dashboard-auth
namespace: tekton-pipelines
labels:
app: tekton-dashboard-auth
spec:
replicas: 1
selector:
matchLabels:
app: tekton-dashboard-auth
template:
metadata:
labels:
app: tekton-dashboard-auth
spec:
containers:
- args:
- --provider=github
- --cookie-secure=true
- --upstream=http://tekton-dashboard:9097
- --http-address=0.0.0.0:8080
- --redirect-url=https://tekton-dashboard.sunway.run/oauth2/callback
- --email-domain=*
- --pass-basic-auth=false
- --pass-access-token=false
- --cookie-secret=P4HLB4CQI6dYvkHpbB4cdsdPfPTFMOcWqq6eadjT01A=
env:
- name: OAUTH2_PROXY_CLIENT_ID
valueFrom:
secretKeyRef:
key: username
name: tekton-dashboard-auth
- name: OAUTH2_PROXY_CLIENT_SECRET
valueFrom:
secretKeyRef:
key: password
name: tekton-dashboard-auth
image: quay.io/oauth2-proxy/oauth2-proxy:latest
name: oauth-proxy
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop: [ "ALL" ]
runAsNonRoot: true
seccompProfile:
type: "RuntimeDefault"
ports:
- containerPort: 8080
protocol: TCP
---
apiVersion: v1
kind: Service
metadata:
name: tekton-dashboard-auth
namespace: tekton-pipelines
labels:
app: tekton-dashboard-auth
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 8080
selector:
app: tekton-dashboard-auth
type: ClusterIP
---
apiVersion: v1
kind: Secret
type: Opaque
metadata:
name: tekton-dashboard-auth
namespace: tekton-pipelines
stringData:
username: Ov12amLAAR34DMGzRkx9
password: 2583dc8bz1350db5aey3521d8703111c2dc67893
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: tekton-dashboard-ingress
namespace: tekton-pipelines
spec:
rules:
- host: tekton-dashboard.sunway.run
http:
paths:
- backend:
service:
name: tekton-dashboard-auth
port:
number: 80
path: /
pathType: ImplementationSpecific
3 DNS Configuration
Add DNS Resolution fortekton-dashboard.sunway.run to your kubernetes entrypoint.
4 Testing
Now you can access to your tekton dashboard withhttps://tekton-dashboard.sunway.run
After you click Sign in with Github and auth success, you will be redirected to your real websitetekton dashboard(upstream), otherwise you will get a 500 error page.
Ref: